- Blog
- Cloud
Multi-Cloud GitOps Automation: From Traditional DevOps to Modern Pull-Based Deployments
The evolution from traditional DevOps to GitOps represents one of the most significant shifts in modern software deployment practices. As organizations increasingly adopt multi-cloud strategies and face growing demands for reliable, secure, and scalable deployments, understanding this transformation becomes crucial for engineering teams worldwide.
The Traditional DevOps Pipeline: A Centralized Approach
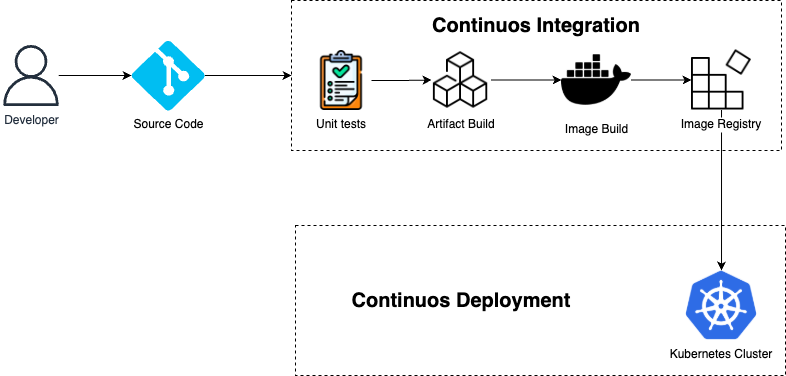
Traditional DevOps pipelines follow a straightforward, linear approach where a single system orchestrates the entire software delivery lifecycle. When developers push code changes, the pipeline immediately springs into action, executing unit tests, building artifacts, creating container images, and pushing them to registries. The same pipeline then takes responsibility for deploying these changes directly into production environments.
This centralized model offers several advantages. Teams receive immediate feedback on their changes, the deployment process remains predictable, and troubleshooting becomes straightforward since everything flows through a single system. However, as organizations scale and security requirements intensify, the limitations of this approach become apparent.
The primary concern lies in the tight coupling between build and deployment processes. The CI system requires direct access to production clusters, creating potential security vulnerabilities. Additionally, when deployments fail, the entire pipeline must be re-executed, often including unnecessary rebuilds of unchanged components.
GitOps: Decoupling Build from Deployment
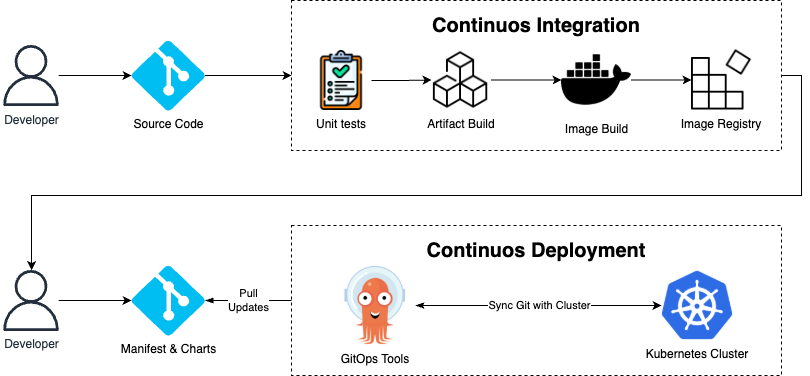
GitOps introduces a fundamental paradigm shift by separating concerns between code integration and deployment orchestration. The continuous integration phase remains largely unchanged—developers still commit code, tests execute, artifacts are built, and images are pushed to registries. However, the deployment story transforms dramatically.
Instead of pushing changes directly to clusters, the CI pipeline updates configuration repositories with new image versions or manifest changes. These Git repositories become the definitive source of truth for what should be running in each environment. GitOps controllers, running within the target clusters, continuously monitor these repositories and automatically synchronize the desired state with the actual cluster state.
This architectural change brings profound benefits. Security improves dramatically since CI systems no longer require cluster access credentials. Deployment history becomes fully auditable through Git commit logs. Rollbacks simplify to Git reverts, and the system gains self-healing capabilities when configurations drift from their desired state.
Push vs. Pull: Two Approaches to GitOps Implementation
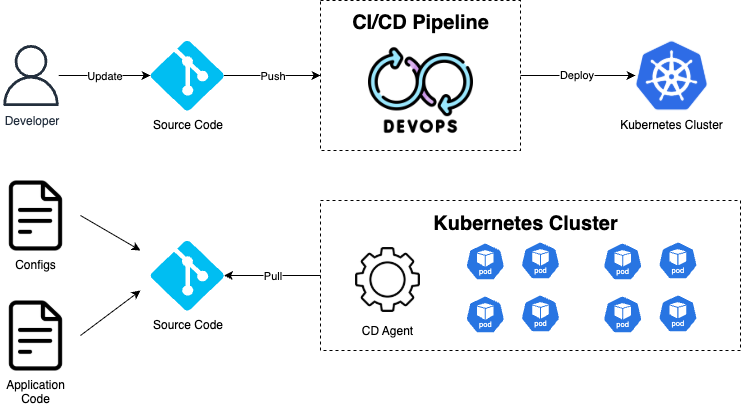
Understanding the distinction between push and pull approaches is essential for implementing GitOps effectively in your organization.
The Push Model: Extended Pipeline Control
The push approach extends traditional CI/CD thinking into the GitOps realm. After updating Git repositories with new configurations, the pipeline continues its execution by deploying changes directly to target clusters. Tools like kubectl or Helm commands execute within the pipeline, pushing the desired state to Kubernetes clusters.
While this approach maintains familiar workflows for teams transitioning from traditional DevOps, it perpetuates some security challenges. The CI system still requires cluster credentials, and any pipeline failures can leave environments in inconsistent states. Scaling across multiple clusters demands complex credential management and increases the attack surface.
The Pull Model: Cluster-Centric Autonomy
The pull approach represents the true spirit of GitOps philosophy. CI pipelines conclude their responsibilities after updating Git repositories. Specialized agents, such as ArgoCD or Flux, operate within each target cluster and continuously poll their designated repositories for changes.
When these agents detect updates, they autonomously pull the changes and reconcile cluster state accordingly. This model eliminates the need for external systems to access cluster credentials, significantly reducing security risks. Each cluster operates independently, enabling better isolation and fault tolerance across multi-cloud deployments.
Scaling to Multi-Cloud Environments
Modern enterprises rarely operate within single cloud boundaries. Multi-cloud strategies have become the norm, driven by requirements for redundancy, cost optimization, regulatory compliance, and avoiding vendor lock-in. This reality demands deployment automation that can handle complexity across diverse cloud environments seamlessly.
Multi-cloud GitOps automation addresses several critical challenges:
Consistency Across Providers: Different cloud providers offer varying Kubernetes implementations and networking models. GitOps ensures that applications deploy consistently regardless of the underlying infrastructure, using standardized manifests and configurations.
Security and Compliance: Each cloud environment may have distinct security requirements and compliance standards. GitOps repositories can maintain environment-specific configurations while ensuring all deployments follow proper approval workflows through Git-based reviews.
Disaster Recovery and Failover: When one cloud region experiences issues, GitOps enables rapid failover by allowing clusters in different regions or providers to pull identical configurations, ensuring business continuity.
Cost Optimization: Organizations can leverage different cloud providers for different workloads based on cost considerations, while maintaining unified deployment processes through GitOps automation.
Implementation Considerations for Your Organization
Transitioning to multi-cloud GitOps automation requires careful planning and consideration of your organization's specific needs:
Repository Structure: Design your Git repository structure to support multiple environments and cloud providers. Consider separate repositories for different applications or a monorepo approach with clear directory structures for each environment.
Secret Management: Implement robust secret management strategies that work across cloud boundaries. Tools like External Secrets Operator or cloud-native secret management services can help maintain security while enabling automation.
Monitoring and Observability: Establish comprehensive monitoring across all your GitOps-managed environments. Understanding the health and performance of deployments across multiple clouds becomes crucial for maintaining reliability.
Team Training and Culture: GitOps represents not just a technical change but a cultural shift. Invest in training your teams on Git-based workflows and ensure they understand the principles behind declarative infrastructure management.
The Future of Deployment Automation
GitOps and multi-cloud automation represent more than just technological improvements—they embody a fundamental shift toward more reliable, secure, and scalable software delivery practices. As organizations continue to embrace cloud-native architectures and multi-cloud strategies, these approaches will become increasingly essential.
The pull-based model of GitOps, combined with proper multi-cloud automation, positions organizations to handle the complexity of modern infrastructure while maintaining the agility and reliability that business demands require. By decoupling build processes from deployment orchestration and leveraging Git as the source of truth, teams can achieve unprecedented levels of consistency and control across their entire infrastructure landscape.
For organizations embarking on this journey, start small with a single application or environment, establish clear GitOps principles, and gradually expand your automation across additional services and cloud providers. The investment in proper GitOps implementation will pay dividends in reduced operational overhead, improved security posture, and enhanced deployment reliability across your entire technology stack.